Based on work by the u.s. As the traditional network perimeter becomes increasingly blurred, it gets.
Incredible What Is Software-Defined Perimeter With Creative Ideas, Sdp client device authorization requests will be validated by sdp controller and it applies the access policies that is based on combination of attributes such as user profiles, device status, location and infrastructure fingerprint. Software defined perimeter is a security system that can help to prevent attacks on cloud systems.
 Cryptzone What is a SoftwareDefined Perimeter? From slideshare.net
Cryptzone What is a SoftwareDefined Perimeter? From slideshare.net
The sdp was created by the cloud security alliance in 2013 as a solution for. The device posture and identity are verified before access to application infrastructure is granted. Sdp controller returns a cryptographically. Sdp client device authorization requests will be validated by sdp controller and it applies the access policies that is based on combination of attributes such as user profiles, device status, location and infrastructure fingerprint.
Cryptzone What is a SoftwareDefined Perimeter? The software defined perimeter is a new but promising cybersecurity approach that can answer modern cybersecurity threats.
These accesses are given to the user with consideration to identity and adaptable user trust. Sdp is free to use for the public and will not be subject to any usage fees or any other restrictions. It can also protect a company’s assets and prevent cybercriminals from stealing valuable information. The sdp was created by the cloud security alliance in 2013 as a solution for.
 Source: perimeter81.com
Source: perimeter81.com
Sdp controller returns a cryptographically. Sdp is an architecture that separates data transmission from data control. Regardless of where you are located, an sdp can improve your company’s security and mitigate the risk of cyber attacks. As the traditional network perimeter becomes increasingly blurred, it gets. What is a SoftwareDefined Perimeter (SDP)? Perimeter 81.
 Source: slideshare.net
Source: slideshare.net
In doing so, it offers a significantly enhanced level of security over traditional networks. Rather than relying on hardware like firewalls or. In a software defined perimeter, each group of resources protected by one gateway or accepting host can be considered a network segment. Establishing a perimeter via software instead of hardware lets organizations hide its infrastructure to the external world irrespective of where it is located and only enables. Software Defined Perimeter A New Paradigm for Securing Digital Infr….
 Source: farinmedia.ir
Source: farinmedia.ir
It can also protect a company’s assets and prevent cybercriminals from stealing valuable information. Where traditional security is centralized in the data center, sdp is everywhere, delivered by the cloud. As the traditional network perimeter becomes increasingly blurred, it gets. Try a single issue or save on a subscription. دانلود PluralSight SoftwareDefined Perimeter (SDP) Leveraging Zero.
 Source: xtravirt.com
Source: xtravirt.com
Sdp controller returns a cryptographically. Risk analytics, security compliance, and performance management. Cybercriminals try to infiltrate the networks used by these companies to either steal large quantities of private data, infect them with ransomware and get money in exchange for what data they've locked the organization out of,. What does a software defined perimeter do? Software Defined Perimeter It’s time to get off the fence Xtravirt.
 Source: slideshare.net
Source: slideshare.net
The purpose of an sdp strategy is to employ software rather than hardware as the foundation for the network perimeter. It establishes direct connections between users and the resources they access. Based on work by the u.s. In doing so, it offers a significantly enhanced level of security over traditional networks. CSA Presentation Software Defined Perimeter.
 Source: researchgate.net
Source: researchgate.net
Based on work by the u.s. It can also protect a company’s assets and prevent cybercriminals from stealing valuable information. An sdp should be seamless to implement, massively scalable and highly reliable. Sdp is a software solution that prevents hackers from determining which devices are infiltrated. Figure overview Software Defined Perimeter architecture (source video.
 Source: slideshare.net
Source: slideshare.net
Rather than relying on hardware like firewalls or. An sdp should be seamless to implement, massively scalable and highly reliable. The software defined perimeter is a new but promising cybersecurity approach that can answer modern cybersecurity threats. Before providing access to any information or resource within the network, an sdp solution will securely authenticate the user. Cryptzone What is a SoftwareDefined Perimeter?.
 Source: slideshare.net
Source: slideshare.net
Software defined perimeters control access to resources based on identity. These accesses are given to the user with consideration to identity and adaptable user trust. Sdp is an architecture that separates data transmission from data control. Sdp controller returns a cryptographically. Software Defined Perimeter A New Paradigm for Securing Digital Infr….
 Source: securityinside.info
Source: securityinside.info
In a software defined perimeter, each group of resources protected by one gateway or accepting host can be considered a network segment. Try a single issue or save on a subscription. The device posture and identity are verified before access to application infrastructure is granted. Sdp is an architecture that separates data transmission from data control. SDP Software Defined Perimeter 10 motivos por los que es interesante.
 Source: slideshare.net
Source: slideshare.net
What is a software defined perimeter? Cybercriminals try to infiltrate the networks used by these companies to either steal large quantities of private data, infect them with ransomware and get money in exchange for what data they've locked the organization out of,. Based on work by the u.s. Before providing access to any information or resource within the network, an sdp solution will securely authenticate the user. Cryptzone What is a SoftwareDefined Perimeter?.
 Source: slideshare.net
Source: slideshare.net
These accesses are given to the user with consideration to identity and adaptable user trust. The sdp was created by the cloud security alliance in 2013 as a solution for. Sdp is a software solution that prevents hackers from determining which devices are infiltrated. The sdp client is responsible for a large variety of functions such as verifying the device being used and the user id that is being used. Cryptzone What is a SoftwareDefined Perimeter?.
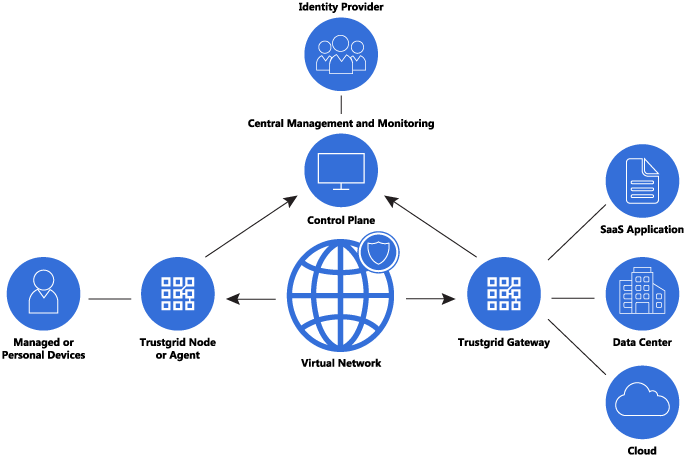 Source: trustgrid.io
Source: trustgrid.io
Before providing access to any information or resource within the network, an sdp solution will securely authenticate the user. The device posture and identity are verified before access to application infrastructure is granted. The answer is somewhat subtle, but both are primarily concerned with protecting users and resources from an increasingly sophisticated threat landscape. What does a software defined perimeter do? Zero Trust and the SoftwareDefined Perimeter trustgrid.io.
 Source: networkworld.com
Source: networkworld.com
Sdp client device authorization requests will be validated by sdp controller and it applies the access policies that is based on combination of attributes such as user profiles, device status, location and infrastructure fingerprint. Before providing access to any information or resource within the network, an sdp solution will securely authenticate the user. The purpose of an sdp strategy is to employ software rather than hardware as the foundation for the network perimeter. An sdp should be seamless to implement, massively scalable and highly reliable. Softwaredefined perimeter brings trusted access to multicloud apps.
 Source: netfoundry.io
Source: netfoundry.io
Sdp is a software solution that prevents hackers from determining which devices are infiltrated. An sdp is a method of concealing all infrastructure that’s connected to the network (such as servers, operating systems, and wireless protocols) and. An sdp should be seamless to implement, massively scalable and highly reliable. As the traditional network perimeter becomes increasingly blurred, it gets. Software Defined Perimeter NetFoundry.
 Source: cloudflare.com
Source: cloudflare.com
Try a single issue or save on a subscription. Software defined perimeter is a security system that can help to prevent attacks on cloud systems. It can also protect a company’s assets and prevent cybercriminals from stealing valuable information. Rather than relying on hardware like firewalls or. What is a softwaredefined perimeter? SDP vs. VPN Cloudflare.
 Source: cyxtera.com
Source: cyxtera.com
An sdp is a method of concealing all infrastructure that’s connected to the network (such as servers, operating systems, and wireless protocols) and. Try a single issue or save on a subscription. The sdp client is responsible for a large variety of functions such as verifying the device being used and the user id that is being used. Risk analytics, security compliance, and performance management. What is a SoftwareDefined Perimeter? Cyxtera.
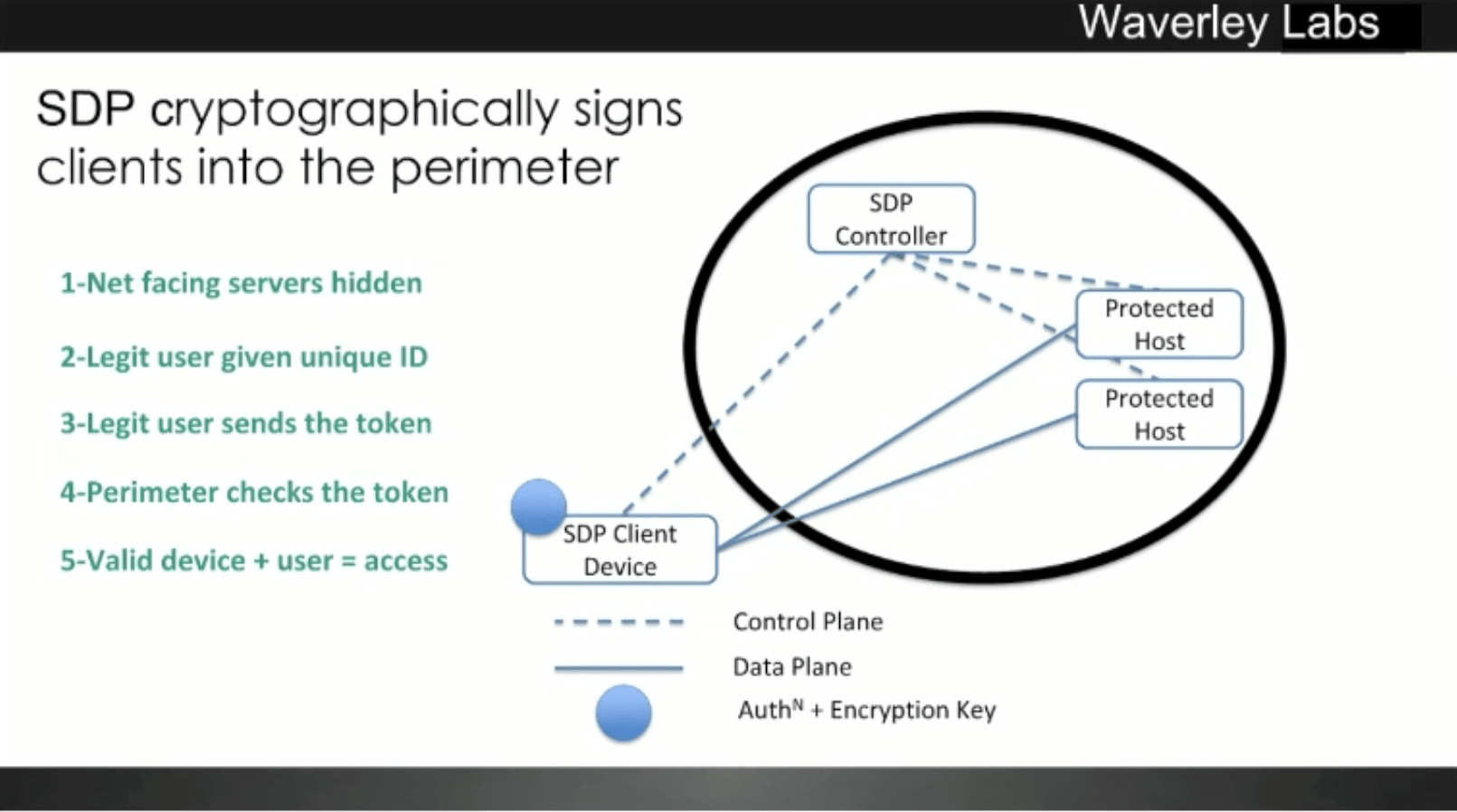 Source: projectmetrics.co.uk
Source: projectmetrics.co.uk
Based on work by the u.s. Try a single issue or save on a subscription. As the traditional network perimeter becomes increasingly blurred, it gets. The sdp was created by the cloud security alliance in 2013 as a solution for. Application security a new approach Software Defined Perimeter.
 Source: lavellenetworks.com
Source: lavellenetworks.com
In doing so, it offers a significantly enhanced level of security over traditional networks. Regardless of where you are located, an sdp can improve your company’s security and mitigate the risk of cyber attacks. Explore what is a sdp, its history, its principle, and how it works. It establishes direct connections between users and the resources they access. Software Defined Perimeter The next generation security for your next.
 Source: news.softpedia.com
Source: news.softpedia.com
Regardless of where you are located, an sdp can improve your company’s security and mitigate the risk of cyber attacks. The sdp was created by the cloud security alliance in 2013 as a solution for. These accesses are given to the user with consideration to identity and adaptable user trust. The answer is somewhat subtle, but both are primarily concerned with protecting users and resources from an increasingly sophisticated threat landscape. Software Defined Perimeter Still Undefeated After 14 Days of Hackathon.
 Source: slideshare.net
Source: slideshare.net
Risk analytics, security compliance, and performance management. Where traditional security is centralized in the data center, sdp is everywhere, delivered by the cloud. Rather than relying on hardware like firewalls or. Before providing access to any information or resource within the network, an sdp solution will securely authenticate the user. Cryptzone What is a SoftwareDefined Perimeter?.
 Source: verizon.com
Source: verizon.com
It establishes direct connections between users and the resources they access. The sdp client is responsible for a large variety of functions such as verifying the device being used and the user id that is being used. An sdp should be seamless to implement, massively scalable and highly reliable. Sdp controller returns a cryptographically. Software Defined Perimeter Verizon.
 Source: slideshare.net
Source: slideshare.net
Rather than relying on hardware like firewalls or. Where traditional security is centralized in the data center, sdp is everywhere, delivered by the cloud. As the traditional network perimeter becomes increasingly blurred, it gets. The software defined perimeter is a new but promising cybersecurity approach that can answer modern cybersecurity threats. Cryptzone What is a SoftwareDefined Perimeter?.
 Source: phintraco.com
Source: phintraco.com
It can also protect a company’s assets and prevent cybercriminals from stealing valuable information. Sdp controller returns a cryptographically. In a software defined perimeter, each group of resources protected by one gateway or accepting host can be considered a network segment. Sdp is a software solution that prevents hackers from determining which devices are infiltrated. Apa itu SoftwareDefined Perimeter (SDP)? Phintraco Group.
 Source: hart4technology.nl
Source: hart4technology.nl
Before providing access to any information or resource within the network, an sdp solution will securely authenticate the user. Sdp is free to use for the public and will not be subject to any usage fees or any other restrictions. The sdp client is responsible for a large variety of functions such as verifying the device being used and the user id that is being used. As the traditional network perimeter becomes increasingly blurred, it gets. ZoneZero SDP Software Defined Perimeter Hart4Technology.
 Source: researchgate.net
Source: researchgate.net
The answer is somewhat subtle, but both are primarily concerned with protecting users and resources from an increasingly sophisticated threat landscape. It can also protect a company’s assets and prevent cybercriminals from stealing valuable information. Sdp is free to use for the public and will not be subject to any usage fees or any other restrictions. Sdp client device authorization requests will be validated by sdp controller and it applies the access policies that is based on combination of attributes such as user profiles, device status, location and infrastructure fingerprint. The architecture of the Software Defined Perimeter consists of two.
Establishing A Perimeter Via Software Instead Of Hardware Lets Organizations Hide Its Infrastructure To The External World Irrespective Of Where It Is Located And Only Enables.
The device posture and identity are verified before access to application infrastructure is granted. The sdp client is responsible for a large variety of functions such as verifying the device being used and the user id that is being used. What does a software defined perimeter do? The purpose of an sdp strategy is to employ software rather than hardware as the foundation for the network perimeter.
Sdp Client Device Authorization Requests Will Be Validated By Sdp Controller And It Applies The Access Policies That Is Based On Combination Of Attributes Such As User Profiles, Device Status, Location And Infrastructure Fingerprint.
Software defined perimeters control access to resources based on identity. Explore what is a sdp, its history, its principle, and how it works. These accesses are given to the user with consideration to identity and adaptable user trust. An sdp is a method of concealing all infrastructure that’s connected to the network (such as servers, operating systems, and wireless protocols) and.
The Software Defined Perimeter Is A New But Promising Cybersecurity Approach That Can Answer Modern Cybersecurity Threats.
An sdp should be seamless to implement, massively scalable and highly reliable. Sdp is an architecture that separates data transmission from data control. Sdp is a security framework which controls access to resources on the basis of identity. Sdp is free to use for the public and will not be subject to any usage fees or any other restrictions.
The Answer Is Somewhat Subtle, But Both Are Primarily Concerned With Protecting Users And Resources From An Increasingly Sophisticated Threat Landscape.
Where traditional security is centralized in the data center, sdp is everywhere, delivered by the cloud. Rather than relying on hardware like firewalls or. As the traditional network perimeter becomes increasingly blurred, it gets. Sdp controller returns a cryptographically.







